How do I protect myself against email scams (phishing)?
In today's online world, scammers are always trying new tricks to steal your information. One of the most common ways they do this is by sending "phishing" emails for a response from an unsuspecting person. These emails attempt to trick you into clicking on a link to their website, downloading a virus-infested attachment, or replying to them with personally identifiable information (PII). They often try to disguise these emails as coming from a ligament company, coworker, or friend.
The best way to protect yourself against these attacks is to be cautious about emails you receive so you can spot these attacks and not fall for them.
Here are a few tips for determining if an email is "phishy" or not. Please note that not all phishing attacks use these tactics and that this is not an exhaustive list.
-
Sender's Address
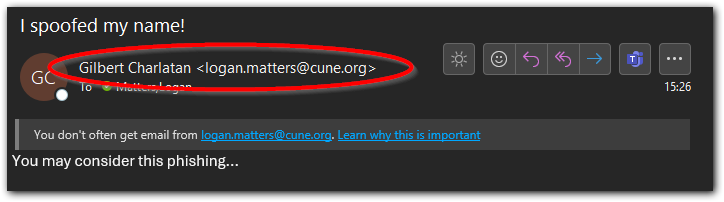
This is the first thing to look at when examining a suspicious email. Examine the address to see if there are spelling mistakes, or if the domain (what comes after the @ symbol) is unusual. Cybercriminals may imitate an email address of someone you know, only changing a character or two. (e.g. helpdesk@cune.edu is legitimate, while helpdesk1@cune.edu or helpdesk@cuna.edu or helpdesk@cune.com are not from us and would be phishing emails)
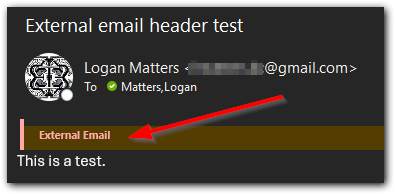
It is also common for the name of an email to be spoofed. You can typically check the actual email address to verify if it is from the person they say they are. There will also be a header included at the top of the email if is from outside our CUNE domain (external email). This is typically the first red flag, but it could still be legitimate if you are expecting communication from someone outside Concordia.
-
Unsolicited
Be cautious of emails coming from something or someone you're not expecting anything from. Some examples we see a lot of are: a Nigerian prince asking you for help with a bank account transfer, your boss asking you to send him a $50 gift card for an office gift, or someone giving away a grand piano but you must pay for the shipping.
-
Urgent
Many phishing attempts try to sound urgent, prompting you to act before you think about the legitimacy of the email. For instance, you get an email from someone claiming to be your boss needing your help with a report and requiring you to send some files over immediately.
-
Generic greeting and signature
Most emails sent to individuals will address the recipient by name, and have a signature of some kind. A "Dear Sir or Ma'am" greeting, along with no signature is a red flag.
-
Spoofed website links
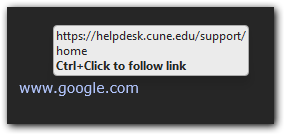
You can spoof a website link and make it look like something else. For instance, www.google.com looks like it goes to Google, but in this case it goes to our Helpdesk homepage. If you hover the link with your mouse, you can see where it actually takes you on the bottom left corner of your window. In outlook, the real link will display next to the spoofed link while hovering your cursor over it, like in the screenshot below.
-
Suspicious attachments
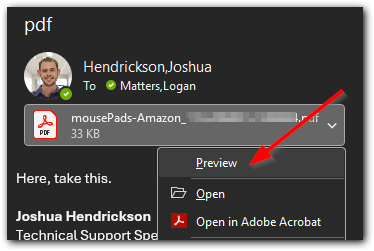
It's easy to put malware in email attachments, so make sure you know an attachment is safe before opening it. The most common one we see are attachments that end in ".htm" but there are others that could be hidden in other more common file types, like PDFs. The preview button in Outlook can be a helpful tool for PDFs from suspicious senders.
-
Poor spelling/grammar
Poor grammar or spelling can be an indicator of a phishing attempt. Reputable businesses are usually careful with spelling and grammar when advertising or communicating with customers.
If you're ever not sure about an email, it's better to err on the side of safety. You might call the person you think is the sender (NOT using the phone number they gave in the email), to make sure they meant to send the email. You can also forward the email to helpdesk@cune.edu, and we'll examine it to make sure it's legitimate.
Note: If you know that an email is phishing, please use the Report button in Outlook, as this will send us more technical information on the email. To use this button, simply look for the shield outline
with an exclamation point inside it. In most contexts this icon is red. Some examples are below.
Outlook for Windows with classic ribbon
Outlook for Web or
Outlook for Windows with simplified ribbon
Outlook for Mobile
Outlook for Mac
![]()
![]()

OR


If you think you might have fallen for a phishing attempt, having clicked on a link or sent sensitive information, please let us know immediately. If you divulged any account information, you should change your password as soon as possible at our account management website: accounts.cune.edu.
For more information on social engineering and phishing, see the National Cybersecurity & Infrastructure Security Agency's tips on cybersecurity: https://us-cert.cisa.gov/ncas/tips